Network security architecture diagram How we built our diy home security camera system Cyber network
Symmetric vs Asymmetric Encryption
Network diagram cisco computer networks architecture examples router gateway example visio wan switch server lan topology drawing conceptdraw wifi picture Solution: network security design diagram It security solutions
Network diagram software isg network diagram
Network gateway routerEncryption symmetric asymmetric using explained aes illustrates encrypting differences definitions hashed ciphertext identical Symmetric vs asymmetric encryptionNetwork topology is the arrangement of the various elements (links.
Network design examplesEncryption network diagram Network diagram computer drawing architecture circuit examples example diagrams smartdraw software infrastructure networking business small secure make wiring interior boardIndex of /~rappleto/classes/cs228.

Network diagram examples and templates
Asymmetric vs symmetric encryption: definitions & differencesNetwork security architecture diagram Networks diagrams encryption conceptdraw system flow controls protect explain premise flowchart san defines policies communications users audit flowchartsSolved f. explain two secure network design principles that.
Analysis of research results of different aspects of network securityA network topology is the arrangement of a network, including its nodes Network diagram cisco topology infrastructure networking architecture examples communication system nodes computer networks arrangement elements software structure its showing createlyRecommended design for a secure network architecture.

Cameras surveillance wiring vueville cctv synology control install networking
Network security diagram wireless computer firewall wan example diagrams secure lan architecture networks clipart between drawing devices conceptdraw networking systemNetwork diagram cisco topology computer networks isg drawing gateway software conceptdraw examples templates wan diagrams example create sample lan area 加密初学者指南。 beginners guide to cryptography.Centralized configuration for microservices using spring cloud config.
Network security diagramsSecurity network diagram architecture firewall example diagrams computer cyber clipart model networks conceptdraw recommended microsoft access solution examples devices infrastructure Encryption data types methods proofpoint definition numbers use place sender between receiver importance takes prime worksEncryption diagram of proposed scheme.

Network diagram lucidchart examples security topology wan lan area local templates chart template networking firewall management wide gif storage networks
Cyber technology security network protection design 1330277 vector artNetwork cisco topology infrastructure networking communication networks logical nodes administrator creately arrangement infrastructures Security network diagram diagrams architecture libraries example solution cybersecurity conceptdraw guide.
.


Recommended Design for a Secure Network Architecture | by Naka | Medium

Symmetric vs Asymmetric Encryption

Solved F. Explain two secure network design principles that | Chegg.com

加密初学者指南。 Beginners Guide to Cryptography. - Quick博客

Analysis of research results of different aspects of network security

Network topology is the arrangement of the various elements (links
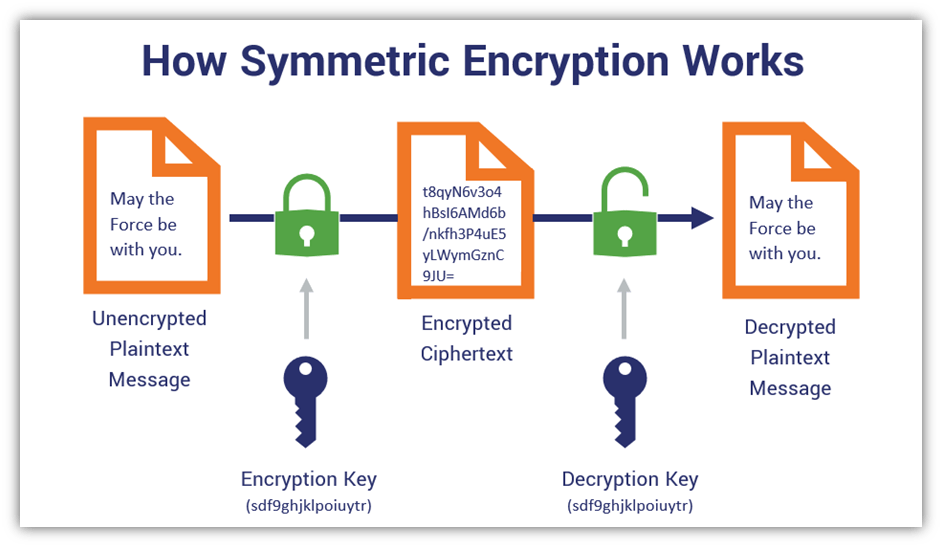
Asymmetric vs Symmetric Encryption: Definitions & Differences - Hashed

IT Security Solutions